Configure Thunderbird 128 e2e encryption with GnuPG
Contents
It took me longer than I would have liked to setup the latest Thunderbird 128 (Supernova!) to use my existing GnuPG-based encryption setup, for a large part because TB defaults to its own more straight-forward built-in defaults for key management, and so I’m going to publish the recipe here to save you some time, hopefully.
All the details, at various levels of obviousness, can be found on this Mozilla wiki page, but here I’m going to make the whole sequence more obvious.
After having followed the steps below, you’ll be able to sign and/or encrypt outgoing emails, and verify and/or decrypt incoming emails.
Update advanced configuration to enable GnuPG use
Go to settings / general, and then select Config Editor. Type gnupg in the search bar, and then set the following two variables to true:
mail.openpgp.allow_external_gnupgmail.openpgp.fetch_pubkeys_from_gnupg
Set your personal key ID
Go to account settings / end-to-end encryption, click the Add Key button at the top and then in the dialog that appears select Use your external key through GnuPG (e.g. from a smartcard).
After that, you’ll be able to add your key ID (the last 16 characters from your fingerprint):
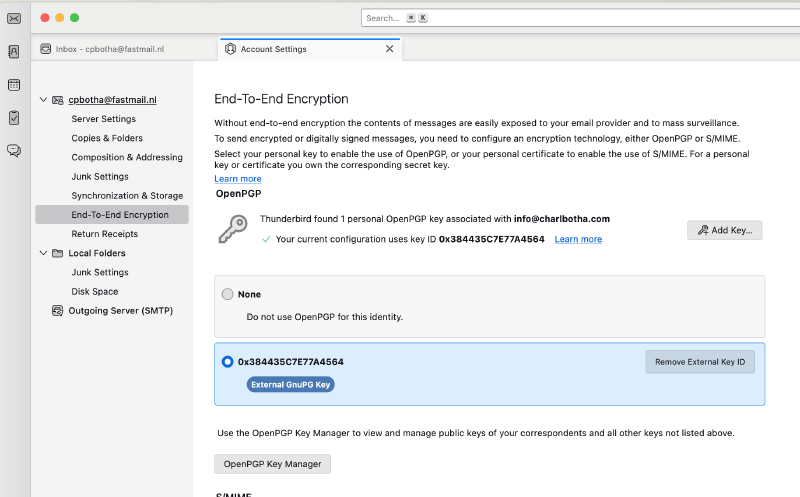
For example, my key fingerprint is 54E725AF4E0D36B86E66359E384435C7E77A4564 and the last 16 characters are
384435C7E77A4564, which I entered without the preceding hex prefix 0x.
Manually import your own public key
Although this Thunderbird is able to import the public keys of correspondents when you request that (see further down), I needed to import my own public key manually.
I did this by invoking:
|
|
… then clicking the OpenPGP Key Manager button on the End-to-End Encryption settings page, invoking *Import public
key(s) from file" (from the File menu) and then selecting the .pgp file you just exported with gpg.
Ensure a usable pinentry app
On macOS, I had to brew install pinentry-mac and then add the following line to my ~/.gnupg/gpg-agent.conf:
|
|
Do whatever is required on your OS.
If you don’t have a suitable pinentry app configured, gpg-agent will not be able to ask for your passphrase when you
sign or decrypt emails.
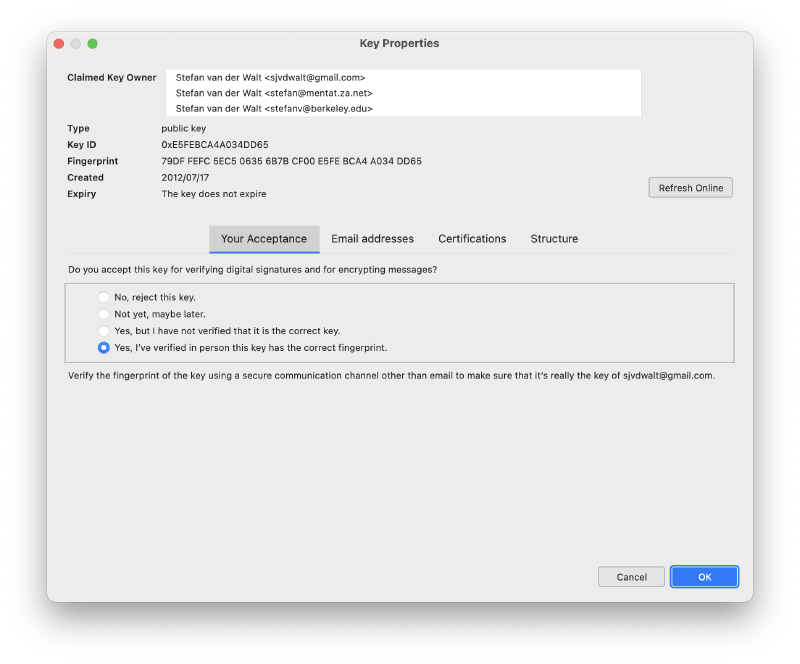
Add public keys of correspondents
With the relevant email open, you can right-click on any correspondent’s name, and then select Discover OpenPGP key from the context menu.
If that person has a public key on the keyserver network, you should be able to import it.
Trust / verification levels are not imported from your GnuPG keyring. I had to do this manually for people aready in my keyring.
Never gonna give you up
There are easily dozens of us who still use OpenPGP email encryption.
Let’s make the most of it!