OpenPGP WKD for easy PGP key discovery
Contents
Web Key Directory (WKD) “is a standard for discovery of OpenPGP keys by email address, via the domain of its email provider”.
In short, through some DNS and files-on-your-webserver conventions, some email clients (e.g. Thunderbird or ProtonMail) and tools like GnuPG are able to retrieve your PGP keys automatically. This is of course super convenient and desirable for your correspondents, because PGP encryption is hard enough as it is.
OpenPGP makes this even better by offering “WKD as a service”, which means you only have to do the DNS bits, and not the files-on-your-webserver bits.
Export your keys to OpenPGP AND VERIFY
Before any of this can work, we need to export our public key to OpenPGP, and, very importantly verify the email addresses associated with them.
Following the documentation, we use gnupg and curl to upload, and get a verification link.
|
|
After running this command, open the verification link, and verify each of the associated email addresses. In short, you click on the verify button, wait for the email, and then click on the link in that email.
Setup your DNS with CNAMEs pointing to OpenPGP
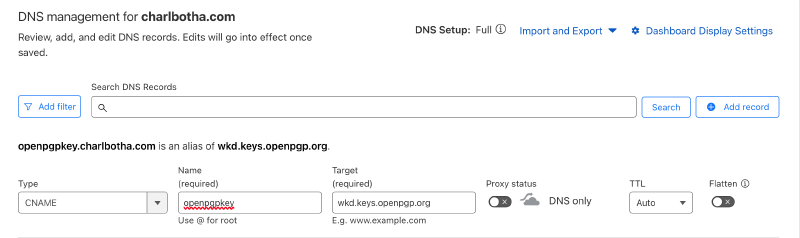
Following the documentation for WKD as a service, create a CNAME openpgpkey subdomain on each of the involved email domains, and point it to wkd.keys.openpgp.org.
I’m currently using CloudFlare for my domains, where this setup looks as follows:
Test and use WKD key discovery
For any domain where you’ve setup this CNAME, you should be able to use something like the following invocation to test WKD retrieval of your key via the email address in question:
|
|
Once this is in place, correspondents with sufficiently modern email clients will be able to retrieve the correct keys automatically.
For future key updates, something like gpg --keyserver hkp://keys.openpgp.org --send-keys 0x384435C7E77A4564 (with your key-id of course) should be sufficient, unless you’ve added more email addresses, in which case you should do the verification dance, and add the new CNAME in the case of a new domain.
2025 Updates
- Friend Stefan has a write-up that also shows how to host WKD yourself and has more details on important WKD and GPG gotchas.
- Web Key Directory is a convenient website for validating any WKD setup through email address search.